

- R&D
- Technology
- Product
- Company
- Customer center
Safe.Privacy
Keeper(Personal information protection)
OVERVIEW
protection solution
As a result of a survey on whether or not they have experienced
personal information infringement over the past year, 96.9% of
public institutions, 93.9% of private companies, and 83.9% of citizens
emphasized the importance of personal information protection.
Source : KISA Personal Informaiton Protection Survey (“21)
-
Personal24.8
information
leakage -
Unauthorized24.3
collection and use
of personal information -
Personal12.7
information
theft
- Continuous occurrence of
personal information leakage
and security accidents - Implementation of measures
to secure personal information
stability - Necessary to comply with laws
and guidelines related to
personal information
FEATURE
-
Real-time detection
and management of
personal informationIt manages personal information files
effectively by searching documents in real
time and notifying users of the presence or
absence of personal information. -
Supporting various
document and image
file formatsIt prevents leakage of personal information in
more various format formats by equipping the
engine module of recognizing document file
format and self-developed character
recognition and supporting image file format. -
Encryption and deletion
of personal information
in possessionIt searches for personal information, encrypts
and deletes personal information, and blocks
in advance unauthorized access by those who
are not personal information handlers and who
are not authorized. -
Various settings
and statistics
It is possible to extract only desired personal
information by specifying various inspection
patterns such as resident registration number,
mobile phone number, business number,
driver's license number, etc., and provides user
convenience with statistical results at a glance. -
Convenience,
prevention of leakage
of important information
and security expansionIt is convenient as important information of
various documents and image files are freely
used in the encrypted status, and security is
expanded through automatic encryption
when a newly created documents are saved.
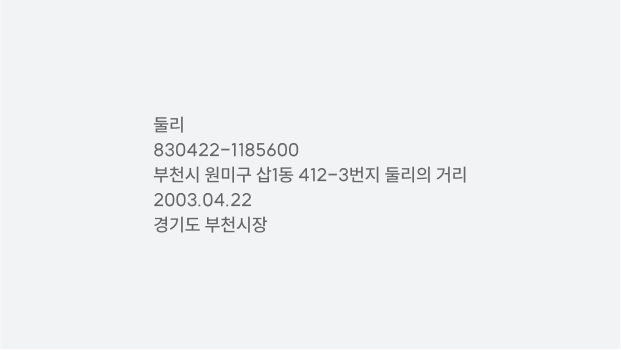
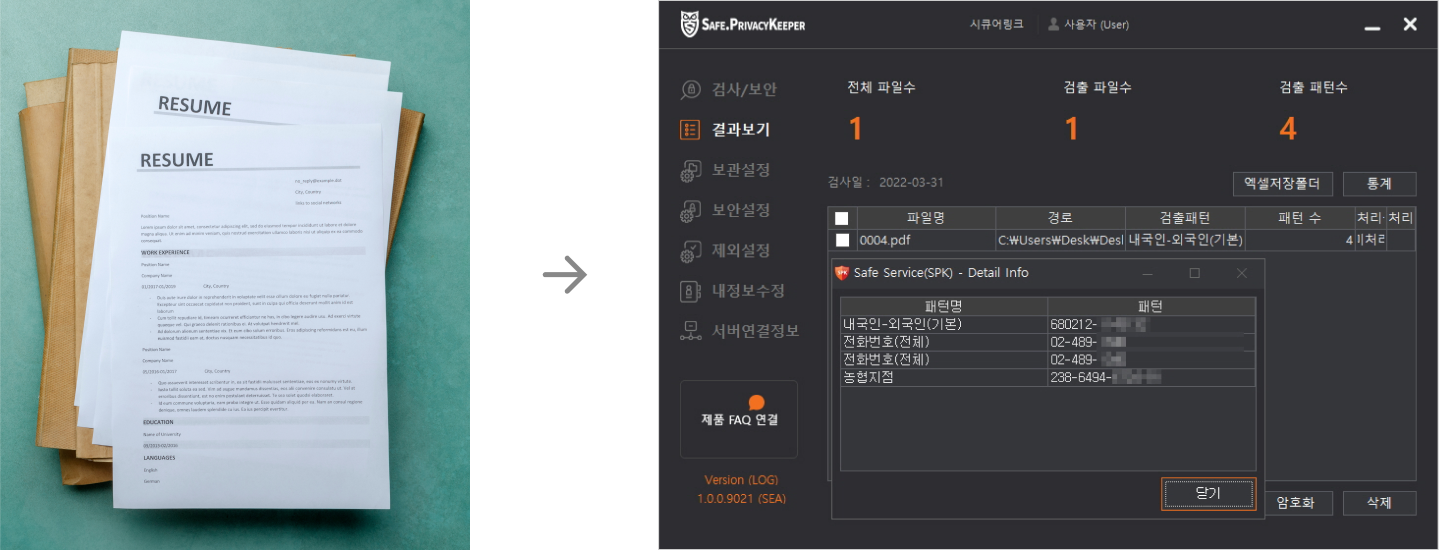
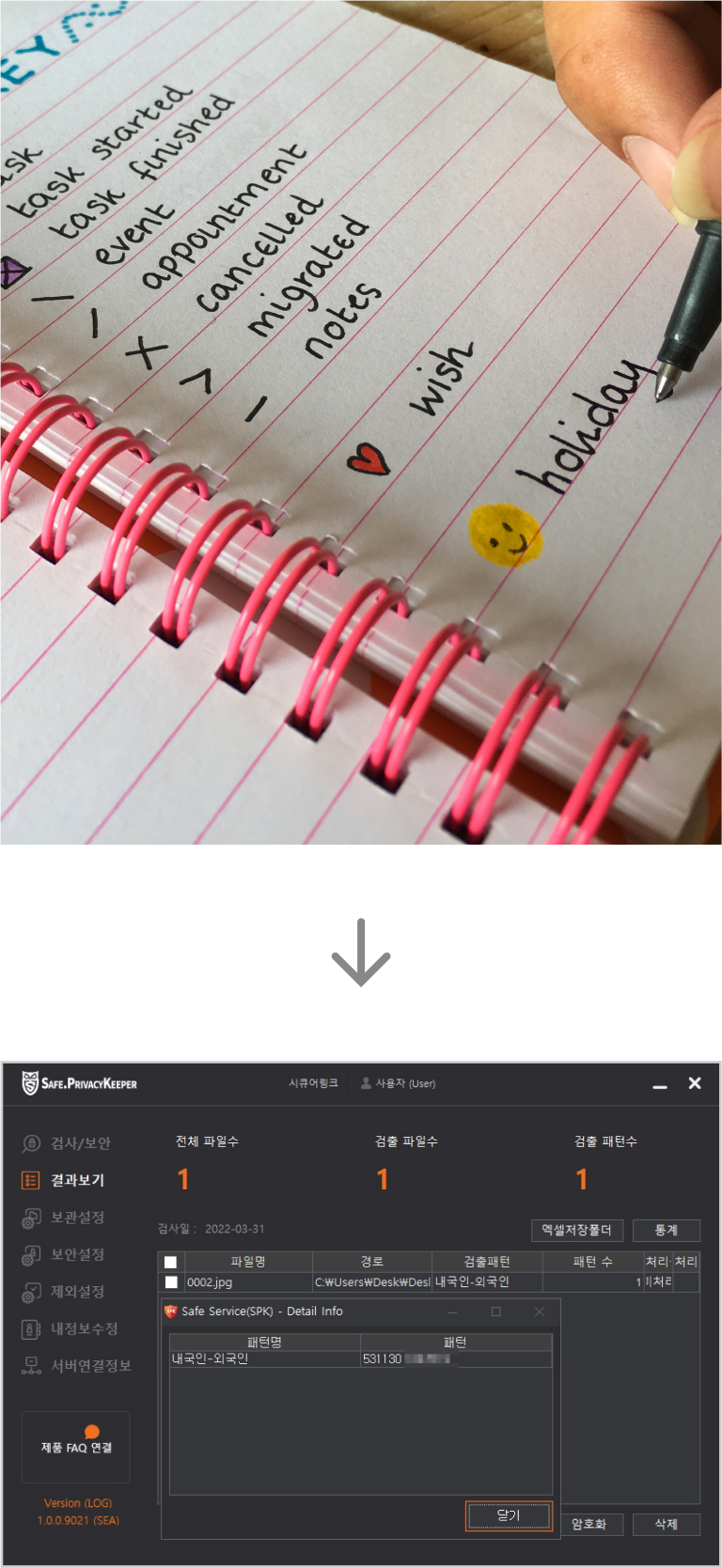
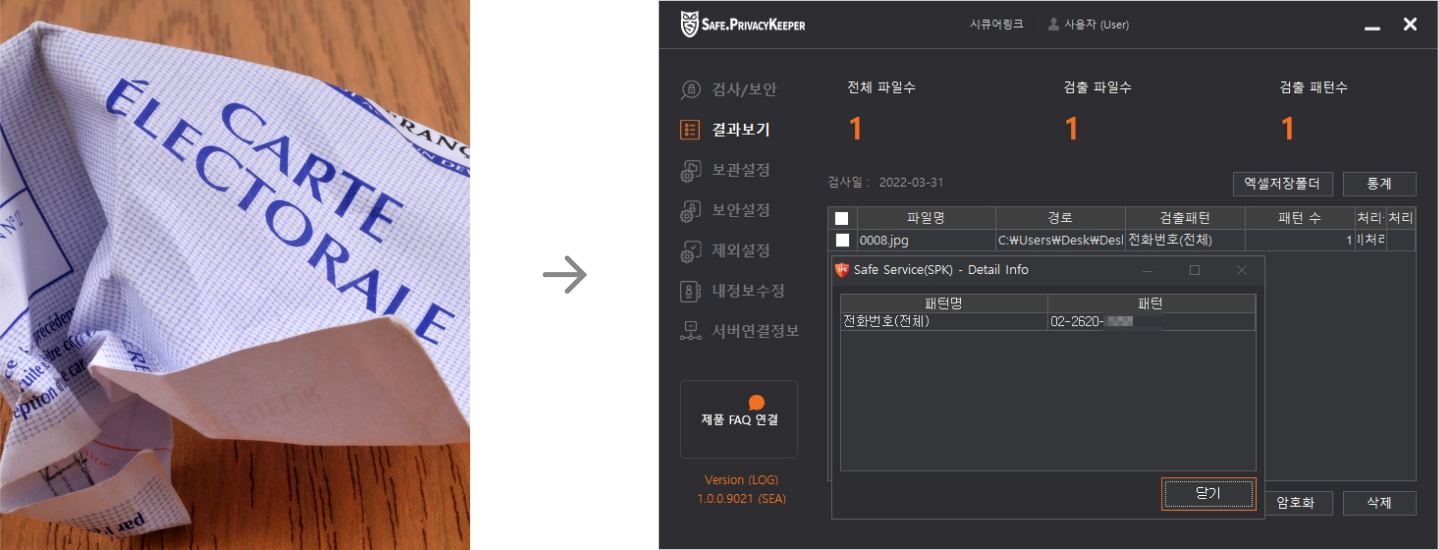
OCR
It paper extracts information corresponding to general characters from images of printed or handwritten
characters and symbols and converts them into digital character information.
-
Printouts or image

-
Change into characters
Sort of OCR
FUNCTION







 TOP
TOP





